Most people know that technology is never 100% secure. One well-known method of obtaining sensitive data is the Rowhammer method, which has been around since 2014. Researchers at ETH Zurich recently published a report on the threat posed by AMD’s Zen 2 & 3 CPUs.
But first, what is Rowhammer? A rowhammer attack is a method in which the bits in dynamic memory can be swapped because the memory cells are so close together and therefore assume the state of the neighboring cell. This results in a so-called bit flip and the whole thing can happen without write access, making it possible to circumvent and exploit security precautions.
In addition to Intel chips, which are also susceptible to this, ETH Zurich has tested AMD’s Zen 2 & 3 chips with Zenhammer, a new Rowhammer version. They used 10 different DDR4 memory bars from the manufacturers Samsung, Micron and SK Hynix. What they found was incredible. They were able to prove that 7 Zen 2 and 6 Zen 3 CPUs were susceptible. Only Intel’s Coffee Lake CPUs performed worse. Before that, it was always said that AMD chips were not susceptible. ETH Zurich explains that simply too few people have looked into this.
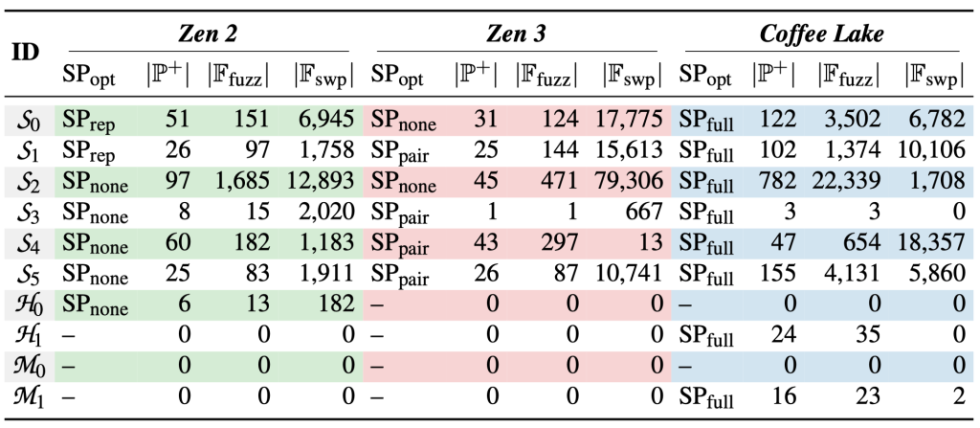
However, AMD has already issued a statement and is already working on a solution to the problem. An update will follow after an extensive investigation. It is not known when this will happen. AMD also recommends contacting the DRAM or system manufacturer to determine the vulnerability to this new Rowhammer variant. However, the company also refers to measures already in place to counteract such an attack.
What is also interesting is that they have even managed to crack a DDR5 memory latch. This is the first public report of DDR5 bit flips on standard systems. However, it was also mentioned that it only worked on one in 10 and further research is needed.
Source: Comsec































5 Antworten
Kommentar
Lade neue Kommentare
Mitglied
Mitglied
Urgestein
Mitglied
Urgestein
Alle Kommentare lesen unter igor´sLAB Community →