Unfortunately, it didn’t just happen to me once: suddenly my own Wi-Fi is no longer reachable, only slowly slow or available several times. Even my mobile phone hotspot has been choked off several times recently. Restart routers, reboot smartphones – it’s all annoying. But what the hell is behind it when something like this happens in a concentrated load? You shouldn’t just become suspicious when there are a lot of student flats in the house.
But always nice in turn, because the following describes one of the possible ways to find out in a self-experiment, e.g. your own router or smartphone is vulnerable to such attacks, which can be successful even if you feel (too) secure in encrypted Wi-Fi.
Important foreword
Since network penetration is a criminal offence in Germany, we have limited ourselves to an attack variant and a tool and also expressly point out that what is shown here and now is only permitted for testing your own wireless network! Disturbing foreign networks and intrusion are prohibited by law and we also assume no responsibility for what readers might gain in knowledge to turn a security check into a serious attack.
No matter which forums or social networks you surf in – various apps and tools always promise one thing: Crash the wi-Fi of your buddy with just one click. Whether you can keep these promises at all is, of course, another question that most people may already be able to answer themselves. These programs are available for any OS, whether Windows, MacOS, IOS or Linux. Either they require an Android root or they are not to be used at all.
Teaching number one: Fingers off such offers that always only want your best, namely your money. Serious troublemakers can only smile tiredly about such glue rods, because it is also really cheap, unfortunately. How about, for example, with a 5 USD tool that keeps these promises without any restrictions? Because in the end we want to test our own routers and smartphones / hotspots and not the suffering of unloved neighbors. Because that is precisely what is forbidden.
What exactly is it all about?
In this article I will show you the death for all those networks where the hardware is vulnerable and how you can of course protect yourself against it in the first place. There are now some instructions on YouTube and you can also gogoogling a lot, but also the technology goes with the times and some details have changed in the approach. That’s why I’ve put together a currently functional version.
This story exploits a specific vulnerability that still exists on many devices, especially with older Android versions or outdated router firmware. The 802.11 WIFI protocol includes a deauthentication frame that can use unencrypted packets to separate clients using a Mac address of the router and client device. To do this, the device only needs to be within range. Connection and password of the network are irrelevant.
This also makes it so dangerous. The target is selected via an interface via the mobile phone with the appropriate attack method, which I will talk about later. Unfortunately, this still works so well, because many manufacturers, especially from the Far East, are reluctant to improve at all. The owners of newer Fritz! By the way, I can calm down boxing, because with the 7-version versions of the Fritz! OS also has no chance of the jammer.
The preparatory steps
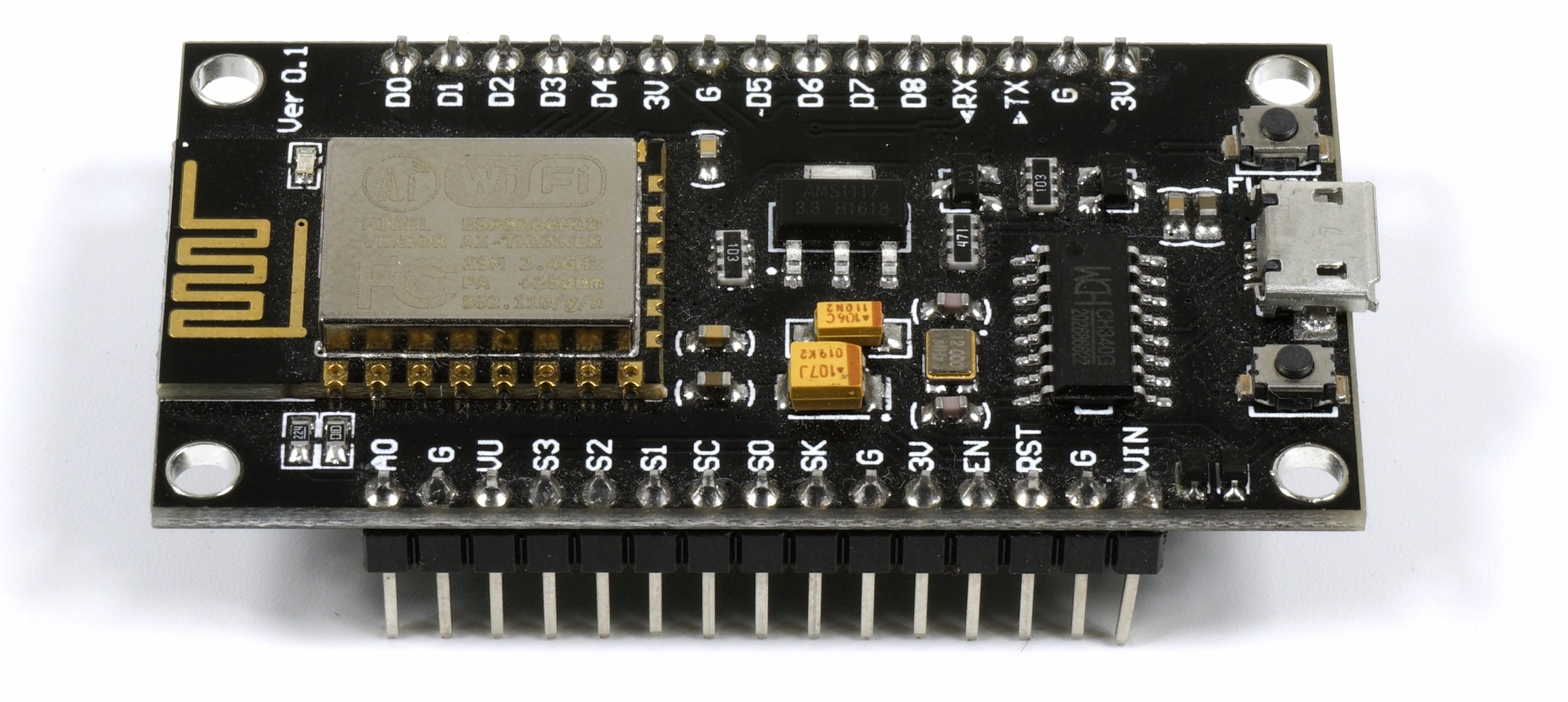
To start, get an ESP8266 and first install Ardunio on your computer. This tool is needed to program the microcontroller. The controller itself is very cheap in every China shop of your choice. Since it is very easy to googling, we for certain reasons do not have a direct link to any shop.
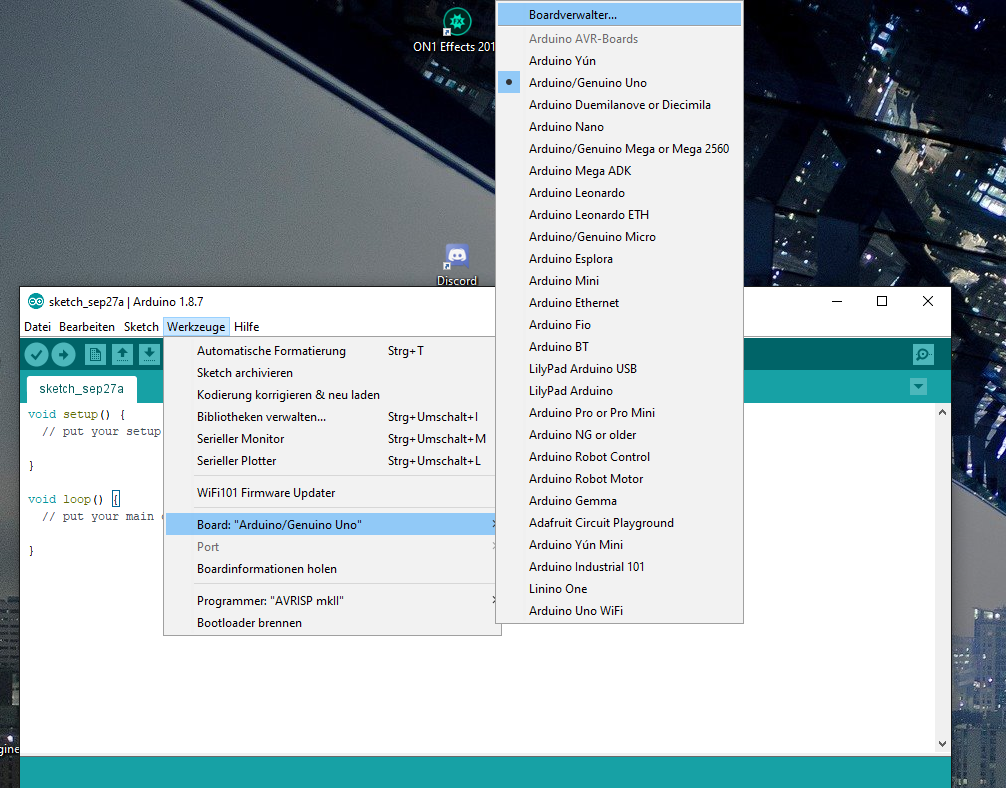
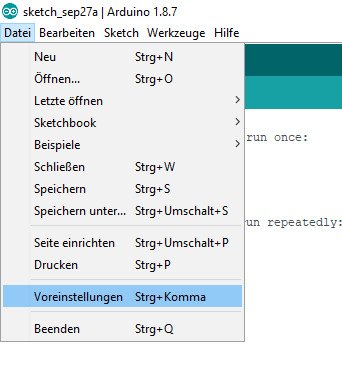
After the installation is complete, you open Arduino and go to “File > Preferences” and insert the link http://arduino.esp8266.com/stable/package_esp8266com_index.json.
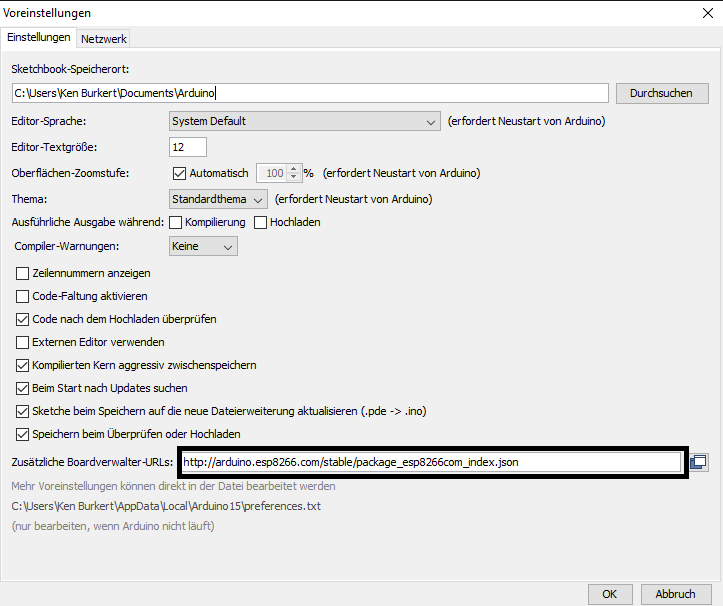
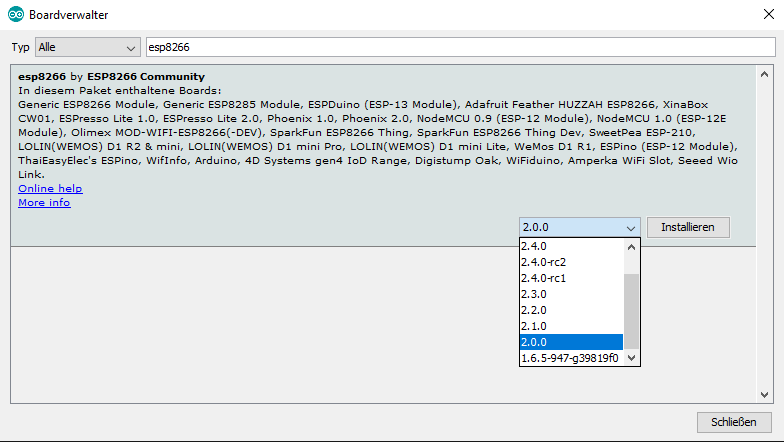
Then switch to “Tools> Board: Arduino>Board Manager” and download version 2.0 for the ESP8266. It is absolutely important to really download version 2.0!
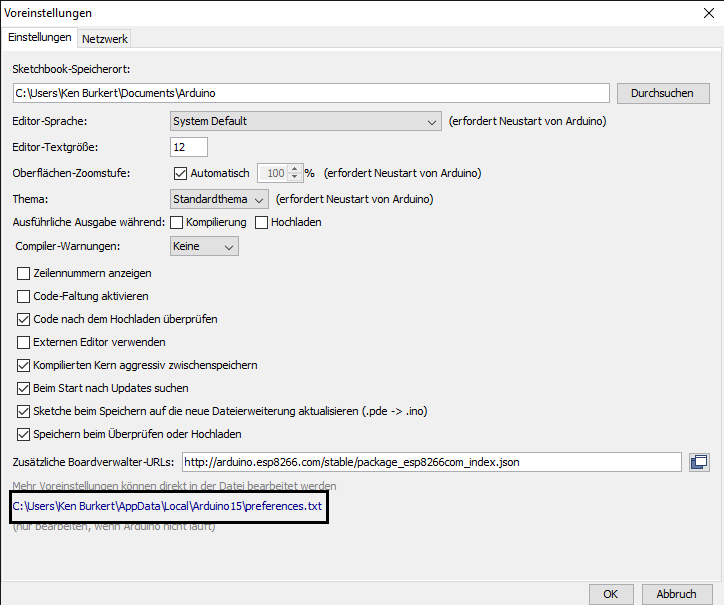
Now let’s navigate back to the preferences and press the file path that appears there.
![]()
now you open the following path: “Packages> esp8266> hardware> esp8266> 2.0.0> tools> sdk> include”…
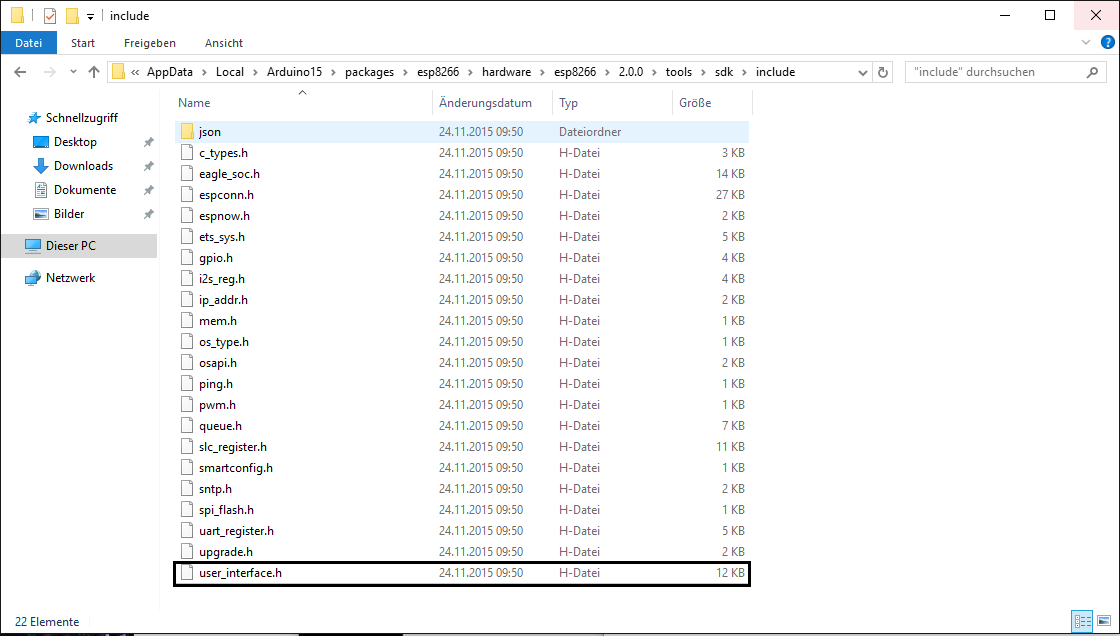
… and then the file: “user_interface.h” with Wordpad or another text editor of your choice.
Now we scroll ahead to #Endif…
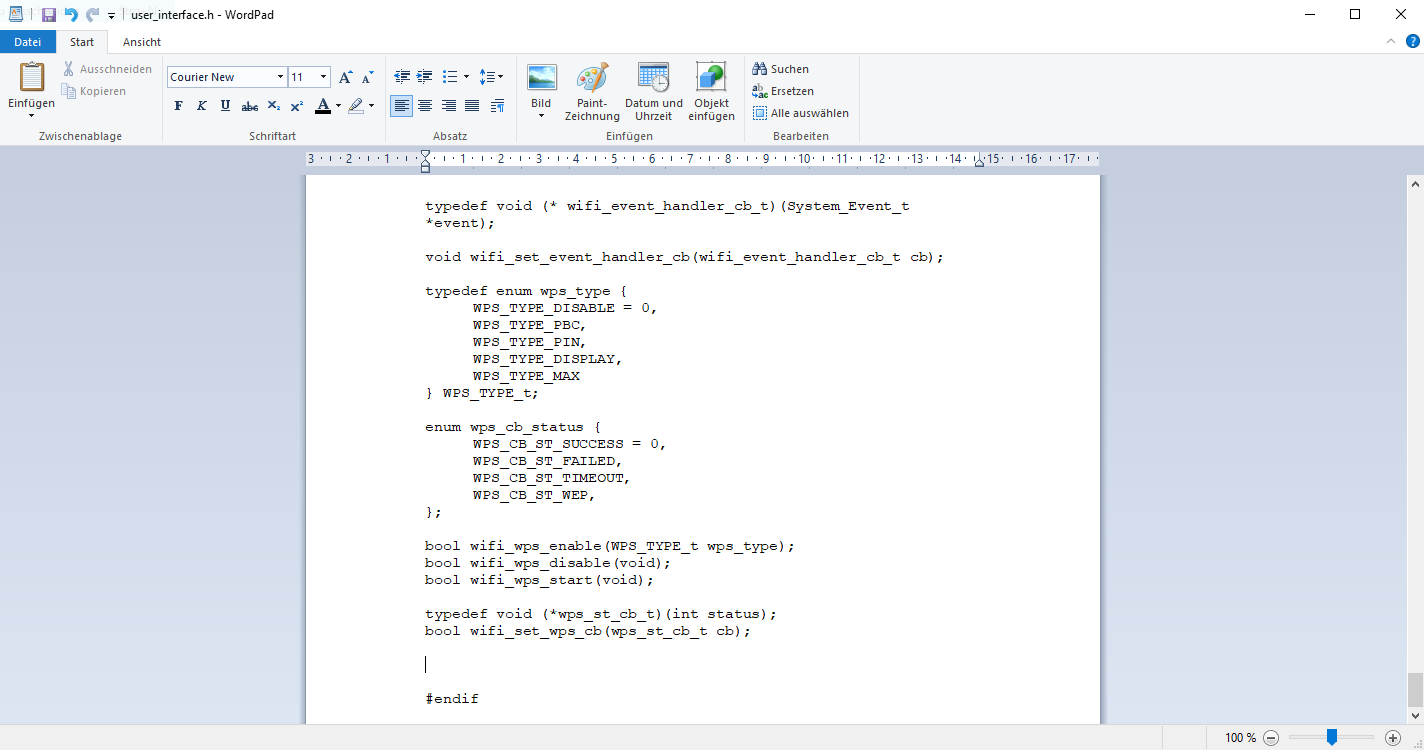
… and insert the following text:
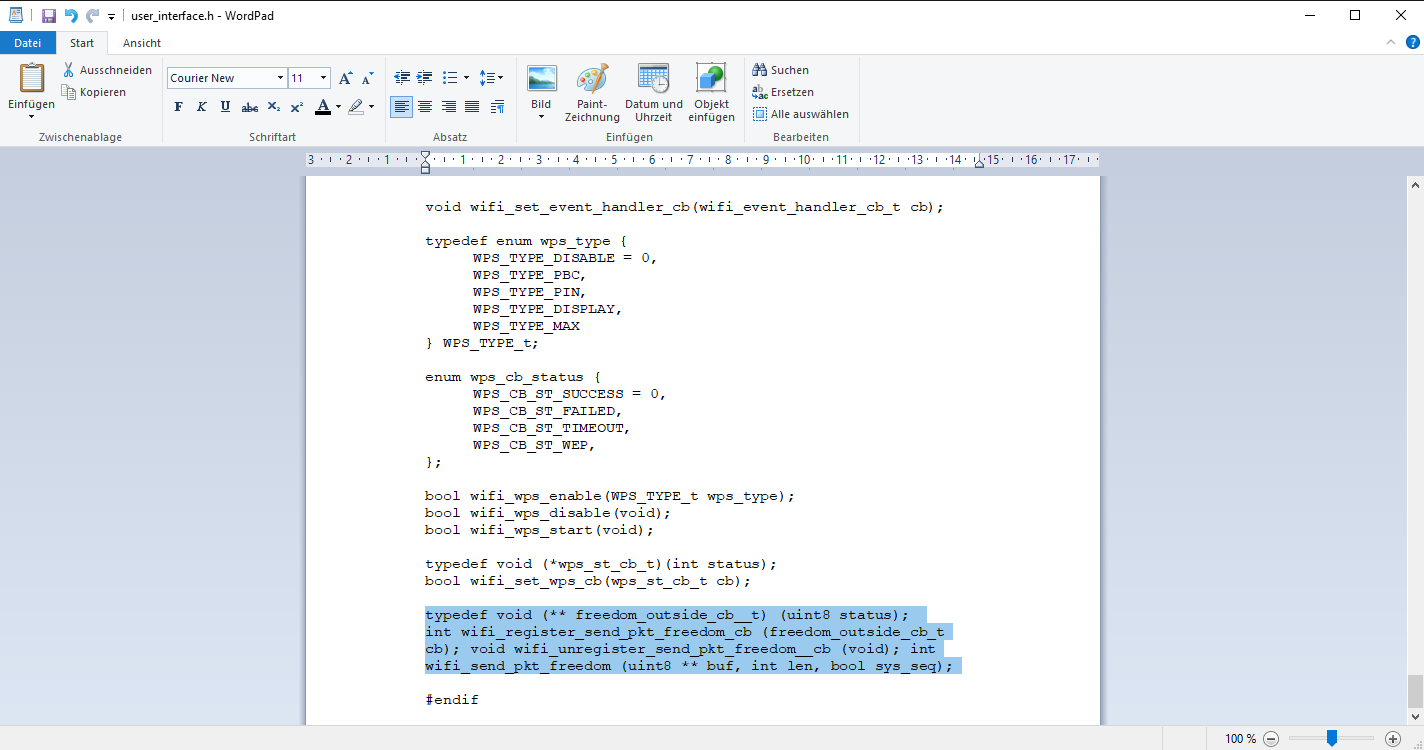
Copy & Paste:
typedef void (** freedom_outside_cb__t) (uint8 status);
int wifi_register_send_pkt_freedom_cb (freedom_outside_cb_t cb);void wifi_unregister_send_pkt_freedom__cb (void);int wifi_send_pkt_freedom (uint8 ** buf, int len, bool sys_seq);
And now please don’t forget to save the whole thing!